Security Center
SECURITY CENTER OVERVIEW
Mechanics Cooperative Bank is committed to protecting your personal account information and reducing the potential for fraud. As a result, we have invested in a Fraud Detection Program that actively tracks transactions associated with your accounts.
The Fraud Detection Programs works around the clock, 365 days per year and includes direct customer communication when necessary. While the Bank would NEVER call and ask you to verify your personal account information (such as your account number or social security number), we may call and ask you to verify recent transactions including merchant location and amount. These verifying phone calls help ensure any possible fraud is detected and removed immediately to limit exposure. We appreciate your cooperation if you ever receive one of these calls.
The Bank will also NEVER send unsolicited emails or other types of communications requesting you to verify any of your personal or financial information. We will never send a link to our website through email without telling you first or without you requesting us to do so.
If you receive a suspicious request please report it to us at report_abuse@mechanics-coop.com.
If you believe that you gave out sensitive information regarding your accounts please call us immediately at 508-823-7744. We appreciate your business and thank you for banking with Mechanics Cooperative Bank.
At Mechanics Cooperative Bank, we prioritize the security and well-being of our customers. We understand fraud can happen to anyone. In the unfortunate event that you suspect fraudulent activity or have fallen victim to a scam, it is crucial to take immediate action.
Below is a list of resources that could aid in protecting you and your accounts:
Mechanics Cooperative Bank Customer Service:
If you believe that you gave out sensitive information regarding your accounts please call us immediately at 1-888-MECHANICS (632-4264).
Filing a Fraud Report with the Federal Trade Commission (FTC):
Click here to file a Fraud Report with the Federal Trade Commission (FTC) on the FTC website: FTC.gov
Reporting Social Security Fraud or Abuse:
To report Social Security Fraud or Abuse, visit the Social Security Administration website here: SSA.gov
Filing a Fraud Report with the Federal Bureau of Investigation (FBI):
To report a cyber crime, visit the Internet Crime Complaint Center (IC3) website here: IC3.gov
Reporting Mail Fraud or Mail Theft:
To report Mail Fraud or Mail Theft, visit the United States Postal Inspection Service (USPIS) website here: USPIS.gov or call 1-877-876-2455.
Massachusetts Attorney General:
Phone: 617-727-8400
Website: Mass.gov
Rhode Island Attorney General:
Phone: 401-274-4400
Website: RI.gov
Mechanics Cooperative Bank will never send unsolicited emails or other types of communications requesting you to verify any of your personal or financial information. We will never send a link to our website through email without telling you first or without you requesting us to do so.
If you receive a suspicious request from us please report it to us at: report_abuse@mechanics-coop.com
If you believe that you gave out sensitive information regarding your accounts please call us immediately at 508-823-7744. We appreciate your business and thank you for banking with Mechanics Cooperative Bank.
Industry reports are being received, of a telephone scam involving fraudsters attempting to obtain personal information from cardholders.
Although no incidents have been reported from our cardholders, we should be informed of these scams and whenever possible, reinforce positive, safe behavior through discussions with our customers.
The details are as follows:
Event Characteristics
Cardholders have received computer-generated calls claiming to be from their financial institution. The calls claim their accounts have been frozen and then direct the cardholder to call a toll-free number to leave their debit card information in order to reactivate any cards. The toll-free number includes a recorded message that asks the customer to key their account number, card expiration date, and PIN.
Recommendations
Cardholder awareness is key in combating fraud. Should our cardholders receive any questionable calls, please make sure they do not provide their personal information. In addition, you may want to share the following tips and/or characteristics of a fraudulent call with our cardholders:
- Make sure you [i.e. cardholder] initiate the contact, and the institution verifies your identity with questions only you would know.
- To verify whether a call is legitimate, call your bank or visit its website, using phone numbers or internet addresses from your bank statement or account documentation. Do not call back a number provided over the phone or click on a link in an email.
- Most communications will include something that will concern or excite the victim.
- If you have been the victim of a scam, file a complaint at local law enforcement.
- Notify your financial institution.
Mechanics Cooperative Bank will never send unsolicited emails or other types of communications requesting you to verify any of your personal or financial information. We will never send a link to our website through email without telling you first or without you requesting us to do so.
If you receive a suspicious request from us please report it to us at: report_abuse@mechanics-coop.com
How Not To Get Hooked by a “Phishing” Scam – Courtesy of OnGuardOnline.gov
“We suspect an unauthorized transaction on your account. To ensure that your account is not compromised, please click the link below and confirm your identity.”
“During our regular verification of accounts, we couldn’t verify your information. Please click here to update and verify your information.”
Have you received email with a similar message? It’s a scam called “phishing” — and it involves Internet fraudsters who send spam or pop-up messages to lure personal information (credit card numbers, bank account information, Social Security number, passwords, or other sensitive information) from unsuspecting victims.
According to OnGuard Online, phishers send an email or pop-up message that claims to be from a business or organization that you may deal with – for example, an Internet service provider (ISP), bank, online payment service, or even a government agency. The message may ask you to “update,” “validate,” or “confirm” your account information. Some phishing emails threaten a dire consequence if you don’t respond. The messages direct you to a website that looks just like a legitimate organization’s site. But it isn’t. It’s a bogus site whose sole purpose is to trick you into divulging your personal information so the operators can steal your identity and run up bills or commit crimes in your name.
OnGuard Online suggests these tips to help you avoid getting hooked by a phishing scam:
- If you get an email or pop-up message that asks for personal or financial information, do not reply. And don’t click on the link in the message, either. Legitimate companies don’t ask for this information via email. If you are concerned about your account, contact the organization mentioned in the email using a telephone number you know to be genuine, or open a new Internet browser session and type in the company’s correct Web address yourself. In any case, don’t cut and paste the link from the message into your Internet browser — phishers can make links look like they go to one place, but that actually send you to a different site.
- Use anti-virus software and a firewall, and keep them up to date. Some phishing emails contain software that can harm your computer or track your activities on the Internet without your knowledge.
- Anti-virus software and a firewall can protect you from inadvertently accepting such unwanted files. Anti-virus software scans incoming communications for troublesome files. Look for anti-virus software that recognizes current viruses as well as older ones; that can effectively reverse the damage; and that updates automatically.
- A firewall helps make you invisible on the Internet and blocks all communications from unauthorized sources. It’s especially important to run a firewall if you have a broadband connection. Operating systems (like Windows or Linux) or browsers (like Internet Explorer or Netscape) also may offer free software “patches” to close holes in the system that hackers or phishers could exploit.
- Don’t email personal or financial information. Email is not a secure method of transmitting personal information. If you initiate a transaction and want to provide your personal or financial information through an organization’s website, look for indicators that the site is secure, like a lock icon on the browser’s status bar or a URL for a website that begins “https:” (the “s” stands for “secure”). Unfortunately, no indicator is foolproof; some phishers have forged security icons.
- Review credit card and bank account statements as soon as you receive them to check for unauthorized charges. If your statement is late by more than a couple of days, call your credit card company or bank to confirm your billing address and account balances.
- Be cautious about opening any attachment or downloading any files from emails you receive, regardless of who sent them. These files can contain viruses or other software that can weaken your computer’s security.
- Forward spam that is phishing for information to spam@uce.gov and to the company, bank, or organization impersonated in the phishing email. Most organizations have information on their websites about where to report problems. You also may report phishing email to reportphishing@antiphishing.org. The Anti-Phishing Working Group, a consortium of ISPs, security vendors, financial institutions and law enforcement agencies, uses these reports to fight phishing.
- If you believe you’ve been scammed, file your complaint at ftc.gov, and then visit the FTC’s Identity Theft website at www.consumer.gov/idtheft. Victims of phishing can become victims of identity theft. While you can’t entirely control whether you will become a victim of identity theft, you can take some steps to minimize your risk. If an identity thief is opening credit accounts in your name, these new accounts are likely to show up on your credit report. You may catch an incident early if you order a free copy of your credit report periodically from any of the three major credit bureaus. See www.annualcreditreport.com for details on ordering a free annual credit report.
Ransomware is a form of malware that encrypts files on a victim’s computer or server, making them unusable. Cyber criminals demand a ransom in exchange for providing a key to decrypt the victim’s files.
Ransomware attacks are becoming more targeted, sophisticated, and costly, even as the overall frequency of attacks remains consistent. Since early 2018, the incidence of broad, indiscriminant ransomware campaigns has sharply declined, but the losses from ransomware attacks have increased significantly, according to complaints received by IC3 and FBI case information.
Although state and local governments have been particularly visible targets for ransomware attacks, ransomware actors have also targeted health care organizations, industrial companies, and the transportation sector.
For more information on Ransomware, please visit Ransomware Tips courtesy of American Bankers Association.
Spyware Quick Facts – Courtesy of OnGuardOnline.gov
Spyware is software installed on your computer without your consent to monitor or control your computer use. Clues that spyware is on a computer include a barrage of pop-up ads, a browser that takes you to sites you don’t want, unexpected toolbars or icons on your computer screen, keys that don’t work, random error messages, and sluggish performance when opening programs or saving files.
To lower your risk of spyware infections:
- Update your operating system and Web browser software, and set your browser security high enough to detect unauthorized downloads.
- Use anti-virus software and a firewall, and keep them up-to-date.
- Download free software only from sites you know and trust. Enticing free software downloads frequently bundle other software, including spyware.
- Don’t click on links inside pop-up windows.
- Don’t click on links in spam that claim to offer anti-spyware software; you may unintentionally be installing spyware.
- Consider using anti-spyware software.
Just when you thought you were Web savvy, one more privacy, security, and functionality issue crops up — spyware. Installed on your computer without your consent, spyware software monitors or controls your computer use. It may be used to send you pop-up ads, redirect your computer to websites, monitor your Internet surfing, or record your keystrokes, which, in turn, could lead to identity theft.
Many experienced Web users have learned how to recognize spyware, avoid it, and delete it. According to OnGuard Online, all computer users should get wise to the signs that spyware has been installed on their machines, and then take the appropriate steps to delete it.
Identity Theft – Courtesy of OnGuardOnline.gov
What to Do If Your Personal Information Has Been Compromised
The bottom line for online threats like phishing, spyware, and hackers is identity theft. ID theft occurs when someone uses your name, Social Security number, credit card number or other personal information without your permission to commit fraud or other crimes. That’s why it’s important to protect your personal information.
If your personal information is accidentally disclosed or deliberately stolen, taking certain steps quickly can minimize the potential for the theft of your identity.
If the Stolen Information Includes Your Financial Accounts
- Close compromised credit card accounts immediately. Consult with your financial institution about whether to close bank or brokerage accounts immediately or first change your passwords and have the institution monitor for possible fraud. Place passwords on any new accounts that you open. Avoid using your mother’s maiden name, your birth date, the last four digits of your Social Security number (SSN) or your phone number, or a series of consecutive numbers.
If the Stolen Information Includes Your Social Security Number
- Call the toll-free fraud number of any one of the three nationwide consumer reporting companies and place an initial fraud alert on your credit reports. This alert can help stop someone from opening new credit accounts in your name.
- Equifax: 1-888-379-4329; www.equifax.com; P.O. Box 740256, Atlanta, GA 30374-0256
- Experian: 1-888-EXPERIAN (397-3742); www.experian.com; P.O. Box 4500 Allen, TX 75013
- TransUnion: 1-800-680-7289; www.transunion.com; Fraud Victim Assistance Division, PO Box 2000 Chester, PA 19022-2000
- An initial fraud alert stays on your credit report for 90 days. When you place this alert on your credit report with one nationwide consumer reporting company, you’ll get information about ordering one free credit report from each of the companies. It’s prudent to wait about a month after your information was stolen before you order your report. That’s because suspicious activity may not show up right away. Once you get your reports, review them for suspicious activity, like inquiries from companies you didn’t contact, accounts you didn’t open, and debts on your accounts that you can’t explain. Check that information — like your SSN, address(es), name or initials, and employers — is correct.
If the Stolen Information Includes Your Driver’s License or Other Government-Issued Identification
- Contact the agencies that issued the documents and follow their procedures to cancel a document and get a replacement. Ask the agency to “flag” your file to keep anyone else from getting a license or another identification document in your name.
- Once you’ve taken these precautions, watch for signs that your information is being misused. For example, you may not get certain bills or other mail on time. Follow up with creditors if your bills don’t arrive on time. A missing bill could mean an identity thief has taken over your account and changed your billing address to cover his tracks. Other signs include:
- receiving credit cards that you didn’t apply for;
- being denied credit, or being offered less favorable credit terms, like a high interest rate, for no apparent reason; and
- getting calls or letters from debt collectors or businesses about merchandise or services you didn’t buy.
- Continue to read your financial account statements promptly and carefully, and to monitor your credit reports every few months in the first year of the theft, and once a year thereafter. For more information on getting your credit reports free once a year or buying additional reports, read Your Access to Free Credit Reports.
- If your information has been misused, file a report about your identity theft with the police, and file a complaint with the Federal Trade Commission at www.consumer.gov/idtheft. Read Take Charge: Fighting Back Against Identity Theft for detailed information on other steps to take in the wake of identity theft.
Free Credit Report
- You may catch an incident early if you order a free copy of your credit report periodically from any of the three major credit bureaus. See www.annualcreditreport.com for details on ordering a free annual credit report.
Debit Card Fraud Notifications:
Protecting your debit card from fraud requires constant monitoring at all hours of the day which is why Mechanics Cooperative Bank now provides free automated fraud detection and alerts for your debit card. If potentially fraudulent transactions are happening with your debit card, we will contact you immediately to confirm the accuracy of these purchases and take any appropriate action as needed.
Please remember: Mechanics Cooperative Bank will never call, text or email you requesting your personal information, including social security number, account passwords or PIN numbers. These fraud detection phone calls will only reference specific purchases made with your debit card and will not ask for any confidential information. If you receive a suspicious phone call or email asking for your personal or confidential information – do not respond. Immediately contact us at 1-888-MECHANICS (632-4264).
What We Are Actively Monitoring:
Debit card transactions are monitored for purchases outside your normal purchasing patterns, unusual timeframes and geographical locations, or purchase patterns that are consistent with previously identified fraud trends.
How Will We Contact You if We Detect Possible Fraud:
How we contact you depends on the phone numbers we have on file. All landlines will receive phone calls and mobile phones will receive text message notifications.
Lost ATM Card: Have you lost your ATM or Debit card? If so, please call 1-833-933-1681 (International: 812-647-9794) or 1-888-MECHANICS (632-4264).
Below please find a list of best practices that can help ensure your safety and security when using ATM’s:
- Do not approach an ATM if suspicious persons are nearby.
- Consider having someone accompany you when the ATM is used later than a half hour after sunset.
- Never approach an ATM after dark if the lights at the ATM site do not appear to be adequate.
- Do not leave your vehicle running or keys in the ignition when using a walk-up ATM.
- Consider canceling the transaction, pocketing your card and leaving if you notice anything suspicious while transacting business at the ATM.
- Minimize time at the ATM by having your card out and ready for use.
- Never leave the ATM with your wallet and/or cash exposed.
- Never give your personal identification number (PIN) to anyone.
- Memorize your PIN. Do not write your PIN on or carry it along with your card.
- Never give your PIN over the telephone. Banks will never ask for your PIN in person or over the telephone.
- Shield the ATM keyboard with your body so others cannot observe the PIN being entered.
- Be sure to take your receipt. It could include personal account information such as account number, balance, etc
- If followed from an ATM, go to an area where there are people and activity.
- Always keep the car running and door locked when using a drive-up ATM.
- When possible, keep at least one car length distance between your car and any vehicle in front of you when waiting to use a drive-up ATM.
- Before lowering your car window to use a drive-up ATM, check for strangers or suspicious persons. If a stranger approaches, drive away from the area at once.
- Report all crimes to the operator of the ATM and to local law enforcement officials immediately.
- Always check the ATM machine for any suspicious devices around or attached to the unit.
Have you received a new contactless debit card? Click here for a list of frequently asked questions and security information regarding your contactless debit card.
For more information on Digital Wallets including Apple Pay, Google Pay, Samsung Pay – Please visit our Digital Wallets page here.
Passwords are unique strings of characters that provide, in conjunction with a User ID, access to an information resource. Passwords are an important aspect of information security because they are the first line of defense in protecting your information online. Passwords are intended to be difficult to guess but still easy to remember. A poorly chosen password may result in the compromise of confidential information that could adversely affect both the Bank and its customers.
General Password Guidelines
Be aware of the characteristics of strong and weak passwords in order to ensure adequate protection of your information online.
Poor, weak passwords have the following characteristics:
- The password contains less than eight characters.
- The password is a word found in the dictionary.
- The password is a common usage word such as:
- Names of family, pets, friends, co-workers, sports, teams, movies, license plate numbers, birthdates, etc.
- Computer terms, names, companies or websites
- Birthdays, social security numbers, User ID and other personal information such as addresses and phone numbers
- Word, number or keyboard patterns like “aaabb,” “qwerty,” “123321”
- Any of the above spelled backwards
Strong passwords have the following characteristics:
- Contain both upper and lowercase letters
- Have digits and punctuation characters as well as letters
- Are at least eight characters long
- Are not a word in any dictionary, language, slang, dialect, jargon, etc.
- Are not based on personal information
As a general practice, you should never write down any passwords. Instead create passwords that can be easily remembered without using any characteristics of a weak password. One way to accomplish this is to create a password based on a song title, affirmation, or other phrase. For example, the phrase might be “Every day I write the book” and the password could be “ED1rtb@@k” or some other variation.
Password Protection
When possible, refrain from using the same password for multiple accounts. Do not share passwords with anyone. The following is a list of things that you should generally NOT do:
- Reveal passwords over the phone to anyone
- Reveal passwords in an email message
- Hint at the format of a password (i.e., “my family name”)
- Reveal passwords on questionnaires or security forms
- Share passwords with family members
- Write passwords down
- Do NOT provide your password to anyone who requests or demands it.
To ensure the safety and privacy of your account information, we provide some key security features in Mobile Banking:
- Unique Activation Code — We send you a unique activation code to verify your phone number. This code associates your mobile phone with your account. This verification also lets you know your mobile phone number has been successfully registered in our system.
- Authentication — You are authenticated for every interaction with Mobile Banking.
- Encryption — All transactions are encrypted.
- Fraud Detection — We incorporate mechanisms such as transaction validation and transaction reconciliation processes to detect fraud.
- Auditability — We provide full audit capabilities through event logs and event-based reporting.
- No Identifiable Information — We don’t return any personally identifiable information in a text message, such as your full account number, e-mail address, or personal address. We never ask for or include your user ID or password in any message we send.
What can I do to increase my security when using mobile banking?
We recommend you take the following steps to increase your personal information security:
- All mobile banking users should password protect their phone to limit unwanted access when left unattended, or lost or stolen.
- Using an app or web based mobile banking platform provides a more secure method of access verses SMS text. To further minimize security risks associated with a mobile browser, such as phishing, website spoofing and man in the mobile attacks, we recommend utilizing our downloadable app for all your mobile transactions.
- Also, be sure when downloading applications to your phone; only download from reputable sources and web sites.
Is my personal or financial information stored on my phone?
No. We don’t save any files with your personal or financial information on your phone. That information stays strictly within online banking. For some phones, such as a BlackBerry, we have logo and branding files that we copy to your phone. Those files do not contain any personally identifiable information.
What if my phone is lost or stolen?
If your mobile phone is lost or stolen, no one can access your account without knowing your password, and, in some cases, your unique user name. To prevent unauthorized access to your account, you can deactivate your phone in Mobile Banking. Go to online banking and access the Mobile Banking pages. On the My Phones page, find the phone number and select the option Stop using this phone for Mobile Banking.
We also recommend contacting your wireless service provider to inquire about a possible “data wipe” of the phone remotely. Often time’s wireless carriers can remotely delete all of the information on your phone including text history, applications, browser history and bookmarks.
How do I disable my phone from access to mobile banking?
You can disable your mobile banking account, or an individual phone, through your Internet Banking account. Simply go to online banking and access the Mobile Banking pages. On the My Phones page, find the phone number and select the option Stop using this phone for Mobile Banking.
Should I access my accounts when using a public, Wi-Fi network connection?
You should never access your account via a wireless local area network (WLANs) or a public Wi-Fi network connection. Most mobile devices can connect to WLANs which allows customers to minimize telecommunication expenses charged through their wireless carrier. Since the network connection is public, we cannot ensure it will be secure and incidents have occurred where personal account information has been stolen from an unsecure WLAN.
Cybersecurity for Small Business – Protecting your Small Business
Mechanics Cooperative Bank is proud to offer our customers access to the Cybersecurity for Small Business Information Center. This online resource center has has been specifically created to provide our customers the opportunity to explore topics of interest related to information and bank account security. Please click the link above and select from the modules available to help better understand and protect yourself from fraud and identity theft. These informational modules were provided on behalf of the Federal Trade Commission and were developed in partnership with the National Institute of Standards and Technology, the U.S. Small Business Administration, and the Department of Homeland Security.
Additional Resources:
Corporate Account Takeover – American Bankers Association (ABA)
Corporate account takeover is a type of fraud where thieves gain access to a business’ finances to make unauthorized transactions, including transferring funds from the company, creating and adding new fake employees to payroll, and stealing sensitive customer information that may not be recoverable. Click the above link to follow the recommended tips provided by The American Bankers Association on keeping your small business safe.
Small Business Cyber Security – U.S Small Business Administration (SBA)
According to a recent SBA survey, 88% of small business owners felt their business was vulnerable to a cyber attack. Yet many businesses can’t afford professional IT solutions, they have limited time to devote to cybersecurity, or they don’t know where to begin. Start by learning about common cyber threats, understanding where your business is vulnerable, and taking steps to improve your cybersecurity.
Elder financial abuse is a growing problem in the United States. Bank employees are trained to notice red flags like unusual recent withdrawals or a new person accompanying older customers to the bank – behaviors that may identify whether or not a customer is vulnerable or currently a victim of financial abuse.
- The American Bankers Association suggests the following tips to help seniors safeguard their money:
- Keep personal information private. Never share your social security number, account information or personal details over the phone or internet, unless you initiated contact with a trusted source.
- Shred! Shred! Shred! Shred receipts, bank statements and unused credit card offers before throwing them away so fraudsters can’t piece together your personal information.
- Don’t let a so-called “advisor” pressure you. Never let a new or un-trusted “advisor” pressure you into sharing personal or financial details. They could be a fraudster. Carefully choose a trustworthy person to act as your agent in all estate-planning matters.
- Lock up your checkbook, account statements and other sensitive information when others will be in your home.
- Get to know your banker and build a relationship with the people who handle your finances. They can look out for any suspicious activity related to your account.
- Never pay a fee or taxes to collect sweepstakes or lottery “winnings.”
- Check references and credentials before hiring anyone. Don’t allow workers to have access to information about your finances.
- Pay with checks and credit cards instead of cash to keep a paper trail.
- Trust your instincts. Exploiters and abusers often are very skilled. They can be charming and forceful in their effort to convince you to give up control of your finances. Don’t be fooled—if something doesn’t feel right, it may not be right. If it sounds too good to be true, it probably is.
For more information on scams and fraud, visit AARP.
To report suspected elder abuse or exploitation in Massachusetts, call 1-800-922-2275.
Mechanics Cooperative Bank engages our community on social media platforms, such as Facebook, Twitter, Instagram and LinkedIn that enable online sharing and collaboration among users who have registered to use them. Any content you post, such as pictures, information, opinions, or any personal information that you make available to other participants on these social platforms, is subject to the Terms of Use and Privacy Policies of each respective platform. Users should refer to those social media platforms, specifically, to better understand your rights and obligations with regard to such content.
Previous Scams & Updates:
Please be aware of an organized scam attempt to fraudulently impersonate our fraud response system, using “spoofed” phone numbers for calls and texts which are made to appear to be from Mechanics Cooperative Bank. Mechanics Cooperative Bank will NEVER call, text, or email asking you to verify or provide specific personal account information. In addition, be cautious of links in texts and emails.
The fraud perpetrators using spoofed phone numbers inform the customer that there is fraud detected on their debit card/account and ask them to verify a fake transaction that did not happen. When the customer denies the transaction, they may be asked to provide information from their debit card, an “online passcode”, a “Secure Access Code” or other banking credentials/personal information. If the customer responds that they do not have an “online passcode”, they may be instructed to create one and provide the fraudster with the multifactor authentication (MFA) code sent to their phone or email.
We take the security and privacy of our customers very seriously and it is crucial that you remain vigilant and cautious while interacting with any text message claiming to be from Mechanics Cooperative Bank or another financial institution.
Sample Text Messages:
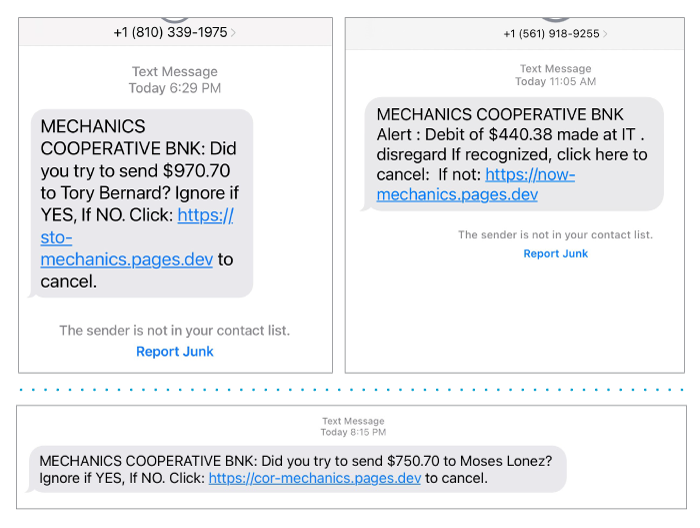
Here are a few key points to remember and follow to safeguard yourself against such scams:
1. Official Communications: Mechanics Cooperative Bank will never ask you to provide personal or sensitive information, such as your account number, PIN, password, or social security number, through unsolicited text messages. If you receive any such requests, do not respond, and immediately report it to us by calling 1-888-MECHANICS (632-4264) or using report_abuse@mechanics-coop.com.
2. Verify the Source: Always verify the authenticity of any text message claiming to be from our bank before taking any action. You can do this by contacting our customer support at 1-888-MECHANICS (632-4264) or visiting your nearest branch.
3. Reliable Contact Channels: Whenever in doubt, rely on our official website for up to date fraud information or our Internet/Mobile Banking platforms to verify your account information. These channels are specifically designed to offer you a safe and encrypted platform to interact with us.
4. Report Suspicious Messages: If you receive a suspicious text message claiming to be from Mechanics Cooperative Bank, please forward it to our dedicated email address for further investigation: report_abuse@mechanics-coop.com. We appreciate your cooperation in helping us combat fraud.
5. Educate Yourself: Stay informed about the latest fraud techniques and scams by regularly visiting our Security Center located on our website and reading the security alerts we share. This will enable you to identify potential threats and protect yourself from falling victim to fraudsters.
We are working diligently to investigate these fraudulent text messages and take appropriate measures to prevent them from causing any harm. Rest assured, our security teams are actively monitoring the situation to ensure the safety of your personal information.
If you have any concerns or need further assistance, please do not hesitate to reach out at 1-888-MECHANICS (632-4264) or by visiting your nearest Mechanics Cooperative Bank branch. We are here to support you and address any questions or issues you may have.
Thank you for your continued trust and cooperation. With your help, we can create a safer banking environment for everyone.
Please note due to enhanced security measures, as of Monday, July 17, 2023 you may be required to reset your password before logging in.
Important Reminder: Passwords are an important aspect of information security as they serve as your first line of defense in protecting your information online.
If you have any questions, please do not hesitate to contact us directly during normal business hours at 1-888-MECHANICS (632-4264).
Please be aware of attempts to fraudulently impersonate Mechanics Cooperative Bank’s fraud response, using “spoofed” phone numbers for calls and texts which are made to appear to be from Mechanics Cooperative Bank. Mechanics Cooperative Bank will NEVER call, text, or email you, asking you to verify or provide specific personal or account information. Be cautious of links in texts and emails.
The fraud perpetrators using “spoofed” phone numbers inform the customer that there is fraud detected on their debit card and ask them to verify a fake transaction that did not happen. When the customer denies the transaction, they may be asked to provide information from their debit card, an “online passcode”, a “Secure Access Code” or other banking credentials. If the customer responds that they do not have an “online passcode”, they may be instructed to create one and provide the fraudster with the multifactor authentication (MFA) code sent to their phone or email.
Sample Fraudulent Text Messages
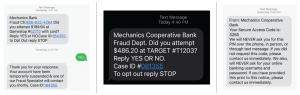
At this point the fraudsters have access to your online banking and debit card information, where they begin to transfer funds and make purchases. The fraudster then informs the customer they will soon receive text messages regarding unauthorized transactions and how to respond, which helps keep the fraud undetected. Calls with the fraudsters may last 30 to 60 minutes.
Mechanics Cooperative Bank will NEVER call, text, or send unsolicited emails requesting you to verify any personal or account information. We will never send a link via email without telling you first, or without you requesting us to do so. If you receive any suspicious requests, hang up the call, don’t click the links, and please report it at report_abuse@mechanics-coop.com or 1-888-MECHANICS (632-4264).
Thank you.
With tax season entering its final stretch, concerns have risen about customer information being exposed through tax preparation offices in local communities. As you know, tax returns contain a wealth of nonpublic personal information (NPPI) including first and last name, home mailing address as well as social security numbers for tax filers. This information can be used in conjunction with other data to open or access bank accounts online and bypass out-of-wallet questions.
One such scheme we learned about recently involved opening accounts online at larger, out-of-state banks and linking them to accounts at community and regional banks operating in Massachusetts. Fraudsters then took advantage of inactive telephonic banking services (more commonly called Voice Response Unit or “VRU”) to approve microdeposits and therefore link the two accounts. Fraudsters then initiated web debits or ACH entries from the out-of-state bank and funds were removed from the account almost instantly.
The complexity of fraud is ever-changing and evolving. Account fraud can be challenging to mitigate. Be sure to check out our end of year checklist which can be helpful not only during tax time, but while reviewing your finances during “Spring Cleaning”.
To download our Year-End Financial Checklists – click here!
If you use need assistance accessing our Telephone Banking system or changing your Telephone Banking PIN – give us a call at 1-888-MECHANICS (632-4264) and a member of our team will be happy to assist.
The Financial Crimes Enforcement Network (FinCEN) is issuing this Notice to alert financial institutions about the potential for fraud, ransomware attacks, or similar types of criminal activity related to COVID-19 vaccines and their distribution.
As of December 28, 2020, the U.S. Food and Drug Administration (FDA) has issued two emergency use authorizations for COVID-19 vaccines in the United States. COVID-19 vaccine fraud may include the sale of unapproved and illegally marketed vaccines, the sale of counterfeit versions of approved vaccines, and illegal diversion of legitimate vaccines.
Already, fraudsters have offered, for a fee, to provide potential victims with the vaccine sooner than permitted under the applicable vaccine distribution plan. In addition, cybercriminals, including ransomware operators, will continue to exploit the COVID-19 pandemic alongside legitimate efforts to develop, distribute, and administer vaccines. FinCEN is aware of ransomware directly targeting vaccine research, and FinCEN asks financial institutions to stay alert to ransomware targeting vaccine delivery operations as well as the supply chains required to manufacture the vaccines. Financial institutions and their customers should also be alert to phishing schemes luring victims with fraudulent information about COVID-19 vaccines.
Additional COVID-19-related information, including advisories and notices, can be found on FinCEN’s website at https://www.fincen.gov/coronavirus, which also contains information on how to register for FinCEN Updates.
Please visit our Coronavirus Update Page for the latest information as it relates to Mechanics Cooperative Bank.